Authentication & Authorization
Zervicepoint relies on federated authentication using Microsoft AD FS or Azure AD FS to protect its resources. The User web and Admin web sites use passive, WS-Federation based authentication, that supports single sign on using Kerberos. Zervicepoint also uses active, WS-Trust based authentication, for communication between the Provisioning engine and the Process system component. Federation in Zervicepoint is configured on a per Store basis which enables multitenancy.
Authentication process
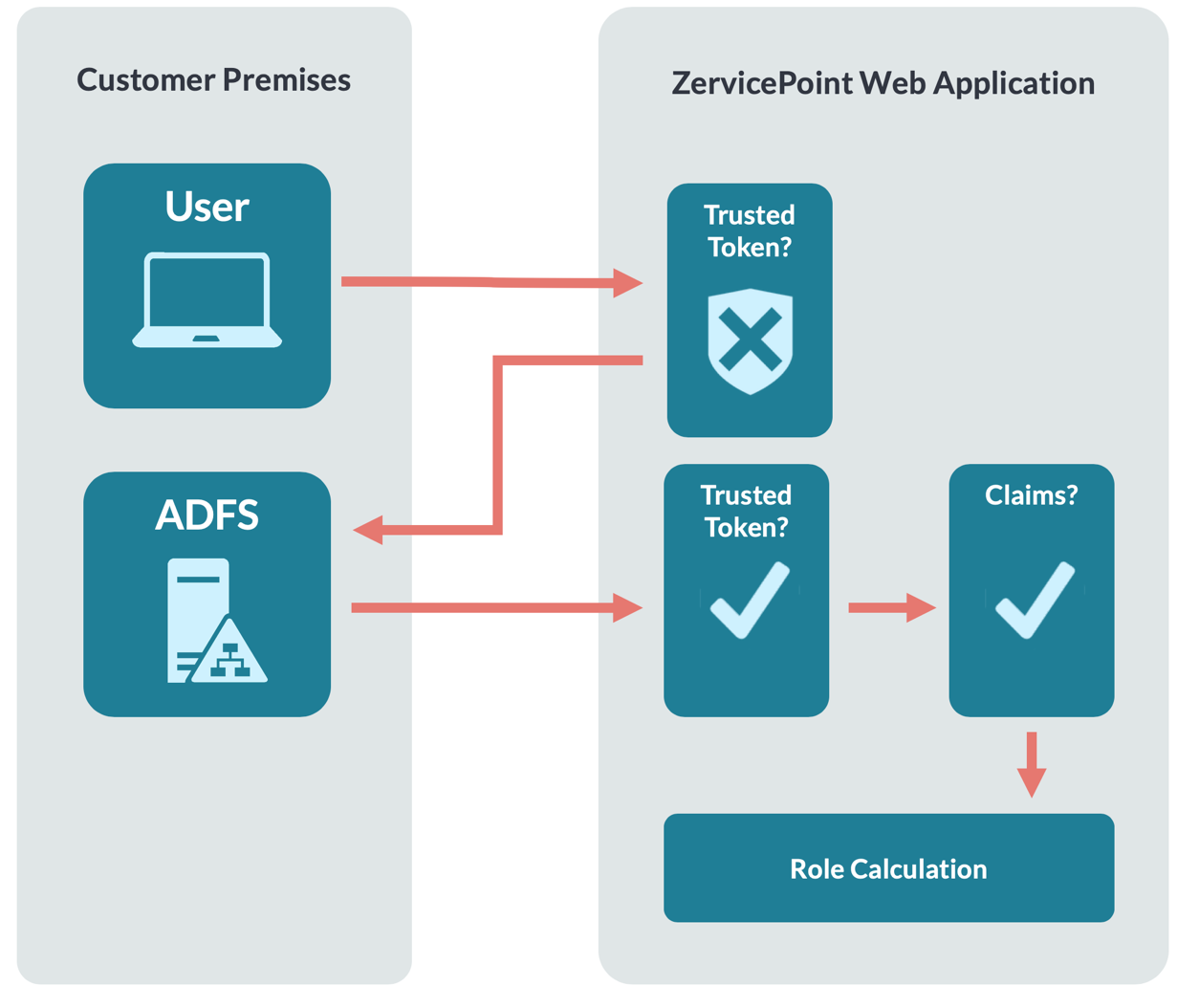
- User browses to the Zervicepoint application and a specific Store.
- User is not authenticated and is therefore redirected to the Issuer (ADFS) configured for the Store.
- The user authenticates at the Issuer, this can be achieved with SSO or by other means depending on configuration and setup. The Zervicepoint application is configured as a relying party at the Issuer.
- The issuer queries for user assertions (Claims) and populates a token and then signs it.
- The issuer posts the signed token (SAML 1.1) back to Zervicepoint.
- Zervicepoint validates token by checking that it is signed by a trusted issuer.
- Zervicepoint validate that the token contains required claims.
- Now the user is authenticated.
- Zervicepoint evaluates which roles the user is a member of, and new claims are added.
Authorization
Zervicepoint utilizes a role-based system for granting access to different parts of the system and for delegation of functionality. Roles are administered from within the administration portal. Membership in a role is controlled either through direct membership or by evaluation of a rule. A rule is a logical expression written in JavaScript that operates on user assertions (claims).